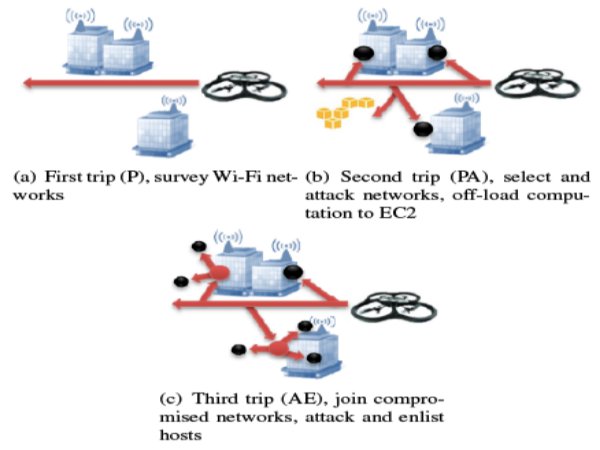
SkyNET is a stealth network that connects hosts to a botmaster through a mobile drone. The network is comprised of machines on home Wi-Fi networks in a proximal urban area, and one or more autonomous attack drones. The SkyNET is used by a botmaster to command their botnet(s) without using the Internet. The drones are programmed to scour an urban area and compromise wireless networks. Once compromised, the drone attacks the local hosts. When a host is compromised it joins both the Internet-facing botnet, and the sun-facing SkyNET.
Subsequent drone flights are used to issue command and control without ever linking the botmaster to the botnet via the Internet. Reverse engineering the botnet, or enumerating the bots, does not reveal the identity of the botmaster. An analyst is forced to observe the autonomous attack drone to bridge the command and control gap.
Attackers bent on espionage could use such drones to find a weak spot in corporate and home Internet connections, says Sven Dietrich, an assistant professor in computer science at the Stevens Institute of Technology who led the development of one of the drones.
The researchers showed that the drone can even be used to create and control a botnet—a network of compromised computers. So instead of controlling a botnet via a command-and-control server on the Internet—a common technique that can lead investigators back to the operator—the hackers can issue commands via the drone. This method creates an “air gap”—the weak spot represented by a wireless network—that could prevent investigators from identifying those responsible for an attack.
Dietrich and two students presented details of their drone, dubbed SkyNet, at the USENIX Security Conference in mid-August. They used a quadricopter—a toy that costs less than $400—to carry a lightweight computer loaded with wireless reconnaissance and attack software. They controlled the homemade drone with a 3G modem and two cameras that send video back to the attacker. It cost less than $600 to build.
The prototype uses a off-the-shelf SBC with an ARM4 250MHz processor. Debian Lenny was used for the operating system. A quad-band Mini-PCI WWAN card was used for the 3G connection and GPS receiver. Two injection-capable Wi-Fi B/G cards were used to connect to the AR.Drone’s Ad-Hoc network and for attacks against Wi-Fi networks. The drone includes a secondary, stronger, GPS receiver. The modifications weigh 196 grams and the AR.Drone was measured and tested to hold a maximum payload of 278 grams. Using the default AR.Drone battery, a 3-cell 1000mAh lithium polymer, the drone can maintain attacks for an average of 2.5 hours. The drone can maintain attacks, while in motion, for an average of 20 minutes.
The drone is piloted through a web interface which shows the controller the output of the AR.Drone’s forward-facing camera, the location via Google Maps, and controls for launching attacks. Piloting the drone over a 3G network allows the controller to position the drone at great distances away from their location. This increases the anonymity of the pilot, but uses an Internet connection. Since the drone is connected to a private 3G network, an Internet proxy must be used for communication. The drone must first negotiate a connection with a proxy before the controller can connect. Additional steps can be taken to preserve anonymity when selecting this proxy. The pilot must make sure they purchase a contract-less network connection for the drone. Although this method of communication is suggested, SkyNET can deliver Command and Control without the use of an Internet connection, simply by separating the duties of the pilot and botmaster.
Detection of new hosts on home networks can prevent the SkyNET enhancement. It is seldom that home networks experience a new connection, authenticating new and returning hosts is a trivial task for routing equipment. Logging these connections and alerting home administrators may be the first step to mitigation
Source: MIT Technology Review, Next Big Future